Get to know Keycloak: The Ultimate Open-Source Solution for Secure Identity and Access Management
Securing user identities and managing access to various applications is nowadays a critical concern for developers and organizations. Managing authentication across multiple platforms can become complex and resource-intensive very quickly, especially with the growing demand for seamless and secure user experiences across various systems and platforms.
This is where Keycloak steps to simplify the process of authentication, authorization, and user management. Developed by RedHat, this open-source solution for IAM, offers enterprise-grade security and scalability without the hefty price tag of proprietary tools.
Whether you’re looking to implement Single Sign-On (SSO), integrate with existing identity providers, or safeguard different APIs, Keycloak provides a robust, scalable framework to handle user authentication and authorization needs with ease. Let’s take a closer look at it!
What is Keycloak?
Keycloak is an open-source identity and access management (IAM) system that was first released in September 2014. There has been continuous development over the past 10 years, and the most recent release, Keycloak 26.0.6 was launched in November 2024.
Keycloak helps developers and organizations manage and secure user authentication and authorization for their applications, simplifying the complexities of identity management by providing solutions for Single Sign-On (SSO), identity federation, and user management, making it a popular choice for enterprise and web applications.
Keycloak is built on top of widely adopted security standards like OAuth 2.0, OpenID Connect, and SAML 2.0, ensuring secure and flexible authentication protocols for modern applications. It supports both web and mobile applications and can integrate easily with existing enterprise systems.
How Keycloak Works
Keycloak simplifies authentication by centralizing the login process. Instead of requiring users to log into each application separately, they authenticate just once through Keycloak’s dedicated login page. When users enter their credentials (such as a username and password), Keycloak verifies their identity providing secure login mechanisms without requiring developers to implement them from scratch. The platform follows a number of concepts:
Authentication: Keycloak acts as an authentication server where users authenticate once, and then they can access multiple applications without having to log in again (SSO – Single Sign-On). It supports various authentication mechanisms, such as username/password, multi-factor authentication (MFA), social logins (e.g., Google, Facebook), and even biometric authentication.
Token Issuance: Upon successful authentication, it generates a one-time verification code that the application retrieves and exchanges for an ID token, access token, and refresh token. These tokens (e.g., JSON Web Tokens – JWT) determine the user’s access rights, allowing the system to grant or deny entry based on predefined roles and permissions. This enhances security, and improves the user experience by reducing the need for multiple logins.
Authorization: Keycloak manages user roles, permissions, and groups to enforce fine-grained access control in applications. It supports both role-based access control (RBAC) and attribute-based access control (ABAC).
Identity Federation: Through identity brokering, Keycloak allows different identity providers (e.g., Facebook, Google, or corporate LDAP systems) to authenticate users.
User Federation: Keycloak can integrate with external user directories like LDAP or Active Directory to allow users to authenticate and access applications using existing credentials.
Key Features
Keycloak offers a wide array of features that make it a versatile and powerful IAM solution. Some of its key features include:
Single Sign-On (SSO)
How it works: Users authenticate once and can then access all authorized applications without needing to log in again.
Why it matters: This reduces login fatigue for users, enhancing productivity by providing seamless access across applications.
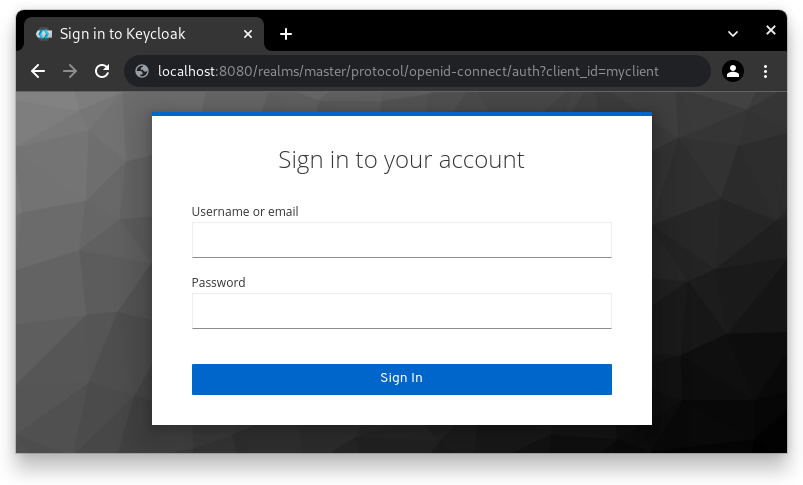
Identity Brokering and Social Login
How it works: Keycloak can act as a broker between different identity providers (IdPs), using protocols like OpenID Connect and SAML 2.0 and/or well-known public IdPs (Google, Facebook, GitHub, etc.).
Why it matters: This reduces login fatigue for users, enhancing productivity by providing seamless access across applications.This allows users to log in with their existing credentials from third-party IdPs such as Google, Facebook, or enterprise IdPs but still use Keycloak’s authorization mechanisms.

User Federation
How it works: It allows organizations to link to external user directories such as LDAP and Active Directory to authenticate users without duplication.

Multi-Factor Authentication (MFA)
How it works: It allows the use of MFA, by requiring users to authenticate using more than just their password (e.g., OTP or authenticator app).
Fine-Grained Authorization
How it works: Role-based access control (RBAC) allows administrators to define permissions for users based on their roles, while attribute-based access control (ABAC) evaluates access decisions based on user attributes, environmental factors (such as time, location, or device), and resource properties.
Customizable Password Policies
How it works: Administrators can enforce custom password rules, including complexity, expiration, and history.
API Security
How it works: Keycloak supports OAuth 2.0, OpenID Connect, and SAML 2.0 for securing RESTful APIs.
Keycloak Components
Keycloak is composed of several key components that work together to provide a seamless identity management solution:
Keycloak Server: The central part of the system, responsible for managing users, handling authentication flows, issuing tokens, and managing configuration for clients (applications) and identity providers.
Admin Console: A web-based user interface that allows administrators to configure realms, clients, users, roles, and other settings in the Keycloak server. It centralizes control, making it easy to configure access policies and monitor user activity.
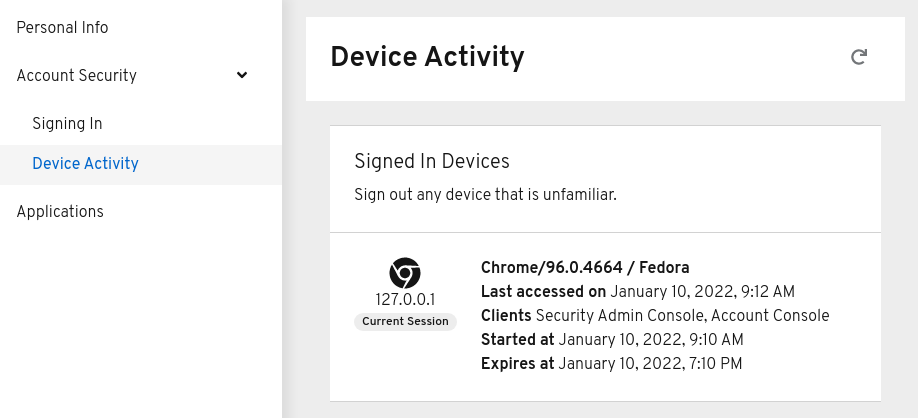
Account Management Console: A user interface that allows end-users to manage their own accounts, change passwords, update personal information, and enable two-factor authentication.
Identity Providers (IdP): Keycloak can integrate with external identity providers to authenticate users from other systems. This could include OAuth 2.0 or SAML 2.0-based providers such as Google, Facebook, or corporate Active Directory.
Clients: Applications (web apps, mobile apps, etc.) that are protected by Keycloak and interact with it for authentication and authorization. Keycloak supports a wide range of client types (e.g., public clients, confidential clients).
Realms: A realm is an isolated environment within Keycloak where all the identities (users, groups, roles, etc.) and configurations are stored. Multiple realms can exist within the same Keycloak instance, making it easy to manage multiple applications or clients with different user bases.
Service Accounts: These are non-human users that can authenticate in an automated fashion for backend services or microservices. They are often used in service-to-service authentication scenarios.
Use Cases
Enterprise Single Sign-On (SSO)
Large organizations often have multiple internal applications – such as HR systems, intranets, and collaboration tools – that require user authentication. Keycloak provides SSO capabilities, allowing employees to authenticate once and gain access to all authorized applications without re-entering credentials. This reduces login fatigue, improves productivity, and minimizes IT support requests related to forgotten passwords.
Customer Identity and Access Management (CIAM)
Companies with customer-facing applications, such as e-commerce websites or customer portals, need a secure way to manage user accounts.
Keycloak supports CIAM by enabling social login, customizable registration flows, and self-service account management. Customers can log in using their existing social media accounts or register directly, while administrators can enforce security policies like multi-factor authentication (MFA).
Microservices Security
Microservices architectures require secure communication between various services, often with different roles and permissions for each service. Keycloak issues OAuth 2.0 tokens for inter-service communication, ensuring that only authorized services can access specific endpoints. It simplifies securing APIs and microservices by managing authentication centrally.
Regulated Industries (Healthcare, Finance, Government)
Industries like healthcare and finance must comply with strict regulations (e.g., HIPAA, GDPR, PCI-DSS) regarding data protection and access control. Keycloak provides robust authentication mechanisms that ensure compliance with regulatory requirements. It also enables detailed audit logging and session management.
Partner and Vendor Portals
Organizations often need to grant access to external partners, vendors, or contractors without giving them full access to internal systems. Keycloak’s identity federation and attribute-based access control (ABAC) allow external users to authenticate via their own identity providers while limiting access based on context-specific attributes (e.g., roles, time, or location).
Multi-Tenant SaaS Applications
SaaS providers need to manage authentication for multiple clients, each with its own set of users, roles, and access policies. Keycloak supports multi-tenancy through realms, allowing each client to have its own isolated authentication environment with customized settings, themes, and policies.
Conclusion
Keycloak is a powerful and flexible identity and access management tool that has become a cornerstone in the open-source community. With its strong security features, ease of integration, and active community, it simplifies the complex tasks of authentication and authorization. Whether for securing web apps, APIs, or microservices, Keycloak offers a comprehensive solution that scales to meet the needs of modern, distributed applications.
By using Keycloak, organizations can avoid reinventing the wheel when it comes to user management and focus on building core features for their products while ensuring high levels of security and compliance by using a centralized point of management.
Ready to implement Keycloak?
If you’re interested in integrating Keycloak into your infrastructure or need expert guidance, click here to contact us! Our team has successfully integrated Keycloak with OpenStack, Gardener and other platforms.

