Navigating the Multiverse: Kubernetes Multi-Tenancy Made Easy
In the vast and ever-expanding universe of cloud computing, Kubernetes has emerged as the go-to orchestrator for managing and scaling containerized applications. One of its superpowers lies in its ability to handle multi-tenancy seamlessly. But what exactly is multi-tenancy, and how does it make your life easier?
Let’s take a closer look at this feature that allows different applications and tenants to coexist harmoniously.
What is Multi-Tenancy?
Multi-tenancy in the cloud means using shared services and resources for multiple clients or users including compute, network, and storage. Picture a bustling apartment building with multiple tenants living under one roof. Each tenant has their own separate space, privacy, and resources, but they all share the same infrastructure including water supply, electricity, etc.
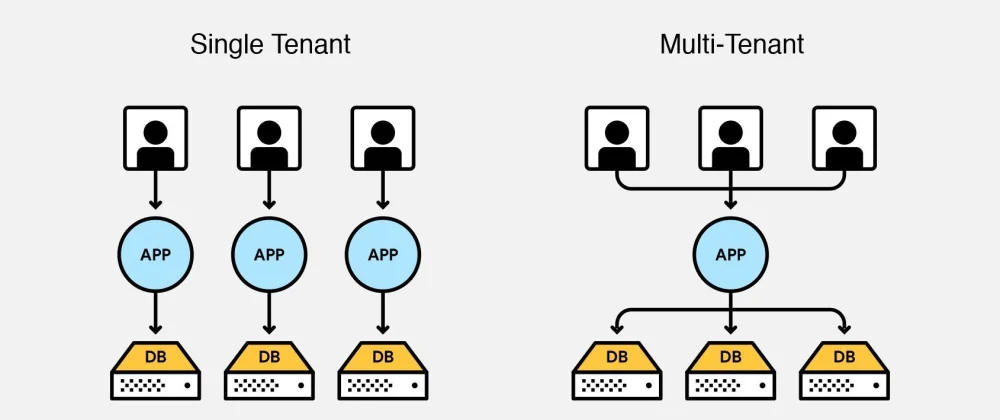
In the world of Kubernetes, multi-tenancy follows a similar concept. It allows you to run multiple applications or services on the same Kubernetes cluster, while keeping them isolated from one another. This isolation ensures that each tenant’s resources and data remain separate and invisible to other tenants, providing a secure and efficient environment.
How Does Kubernetes Enable Multi-Tenancy?
Kubernetes provides various features and components that facilitate multi-tenancy. A Kubernetes cluster consists of a control plane which runs K8s components, and a data plane consisting of worker nodes where tenant workloads are executed. Tenant isolation can be applied to both the control plane and the data plane. The hard isolation with individual clusters per tenant is not in the scope of this post, but depending on the use case might be the best option after all.
Control Plane Isolation
Control plane isolation goal is to ensure that the tenants’ operations, such as creating, updating, and deleting various resources, are isolated and do not interfere with other tenants’ actions. That means that tenants have independent management capabilities.
By isolating the control plane, potential risks of unauthorized access or malicious activities between tenants are minimized. Kubernetes offers three mechanisms to achieve control plane isolation:
Namespaces: Kubernetes namespaces act as virtual clusters within a physical cluster, allowing you to partition resources and create isolated environments for each tenant. It’s like dividing the apartment building into separate wings, each with its own dedicated amenities.
Resource Quotas: Resource quotas enable you to allocate specific limits on CPU, memory, storage, and other resources for each tenant. This ensures fair resource distribution, preventing a single tenant from hogging all the resources, like someone overtaking the building’s elevator.
Role-Based Access Control (RBAC): RBAC is a powerful mechanism in Kubernetes that enables fine-grained access control and authorization. RBAC allows you to define roles and associated permissions for different users or groups within each namespace. This ensures that tenants have appropriate access rights and can only interact with their own resources, enhancing security and isolation.
These three mechanisms are able to partially achieve control plane isolation. However, cluster-wide resources, such as Custom Resource Definitions (CRDs), cannot be well isolated with these mechanisms because, by definition, multi-tenancy should limit access to non-namespaced resources. Thus control plane isolation comes with a limitation that tenants are not able to manage their own CRDs.
Data Plane Isolation
While control plane isolation focuses on the management layer of Kubernetes, data plane isolation deals with the runtime execution of workloads in the cluster. The data plane consists of the actual containers, Pods, and networking infrastructure responsible for running and routing traffic to the applications including Services, Ingresses and more.
Data plane isolation ensures that the resources and network connectivity of each tenant’s applications are segregated and protected. It involves employing mechanisms such as network policies, network namespaces, and container runtime features to create isolated environments for each tenant.
The three main aspects of data plane isolation include:
Network policies that allow fine-grained control over communication between pods and namespaces. They define rules that specify which pods can communicate with each other and which ports and protocols are accessible. By setting up appropriate network policies, tenants can control traffic flow and enforce security measures, preventing unauthorized access or interference from other tenants.
Container runtime features, such as network namespaces and virtual ethernet interfaces, provide isolation at the networking level. Each tenant’s containers are encapsulated within their own Linux kernel network namespaces, ensuring that their network interfaces and IP addresses are isolated and independent from other tenants. Runtimes such as g-Visor allow to further isolate the payload with a concept of an additional “Sandbox” layer between the application running in the container and the Linux host kernel. This layer limits the system calls that an application can do.
Storage isolation should ensure that volumes are not accessed across tenants. Since StorageClass is a cluster-wide resource, reclaimPolicy should be specified as Delete to prevent PVs from being accessed by other tenants. In addition, the use of volumes such as hostPath should be prohibited to avoid the abuse of the nodes’ local storage.
In a nutshell, data plane isolation guarantees that tenants’ applications operate in their own secure and isolated runtime environments, ensuring data privacy, resource allocation, and network security. Advanced network isolation can be achieved through the service mesh.
Benefits of Multi-Tenancy:
Multi-tenancy offers many advantages, making it a popular choice for organizations of all sizes. Let’s explore some of its key benefits:
Resource Optimization: By consolidating multiple applications on a single cluster, you can maximize resource utilization, leading to cost savings and improved efficiency. It’s like fitting all your belongings in a single suitcase for a trip, instead of lugging around multiple bags.
Security and Isolation: Multi-tenancy ensures that each tenant’s data and resources are isolated from others, preventing potential breaches and ensuring data confidentiality. Just like separate apartments with sturdy walls and locked doors, tenants can rest assured that their space is private and secure.
Scalability and Flexibility: Kubernetes enables easy scalability, allowing tenants to seamlessly scale their applications up or down as needed. It’s like having an apartment with expandable rooms that can accommodate your growing needs, without the hassle of moving to a new place.
Simplified Management: With multi-tenancy, you can centralize the management of multiple applications, reducing administrative overhead and streamlining operations. Think of it as having a single landlord to take care of all the apartments, ensuring everything runs smoothly.
Low entry costs: Multi-tenancy in Kubernetes offers low entry costs by enabling infrastructure sharing, optimizing resource utilization, providing scalability, simplifying management, promoting shared services, leveraging pay-as-you-go models, and benefiting from open-source resources.
Challenges of Multi-Tenancy
While Kubernetes multi-tenancy offers many benefits, it also introduces several challenges and considerations. Let’s have a look at some common issues that organizations may face when implementing Kubernetes multi-tenancy:
Resource Allocation and Isolation: Ensuring proper resource allocation and isolation between tenants can be challenging. If not properly managed, resource contention may occur, affecting the performance and stability of critical applications. Allocating appropriate resource quotas and monitoring resource usage becomes crucial to prevent one tenant from negatively impacting others.
Security and Access Control: Maintaining robust security and access control in a multi-tenant environment is vital. Misconfigurations or vulnerabilities in access controls can lead to unauthorized access or data breaches. Proper implementation of Role-Based Access Control (RBAC) and network policies is necessary to enforce access restrictions and prevent cross-tenant interference.
Data Privacy and Compliance: Multi-tenancy raises concerns around data privacy and compliance. Ensuring that tenant data is appropriately isolated and protected is essential to meet regulatory requirements. Implementing encryption, secure storage, and proper data access controls is crucial to maintain data privacy and compliance with relevant regulations.
Tenant Isolation and Noisy Neighbors: Tenant isolation is critical to prevent one tenant’s activities from impacting others. Noisy neighbors, tenants with resource-intensive or poorly optimized applications, can degrade the performance and stability of the overall system. Techniques like resource quotas, workload limits, and monitoring can help mitigate these issues.
Application Compatibility and Dependencies: Different tenants may have varying application requirements, dependencies, or compatibility constraints. Coordinating these requirements while maintaining isolation can be challenging. Careful consideration should be given to manage dependencies, versioning, and compatibility across tenants’ applications.
Complexity and Operational Overhead: Implementing and managing a multi-tenant Kubernetes environment can be complex and require additional operational overhead. Proper planning, monitoring, and automation tools are necessary to efficiently manage the environment and troubleshoot any issues that arise.
Tenant Onboarding and Offboarding: Adding or removing tenants from a multi-tenant environment requires well-defined processes and automation. Ensuring smooth tenant onboarding and offboarding, including resource provisioning, access management, and data cleanup, is important to maintain operational efficiency.
Monitoring and Debugging: Monitoring the health and performance of individual tenant applications, as well as the overall cluster, becomes more challenging in a multi-tenant setup. Effective monitoring, logging and auditing practices, along with proper observability tools, are essential to identify and debug issues across tenants.
To address these issues, organizations need to carefully plan and implement multi-tenancy, considering factors like resource allocation, security measures, compliance requirements, and effective monitoring practices.
Solutions
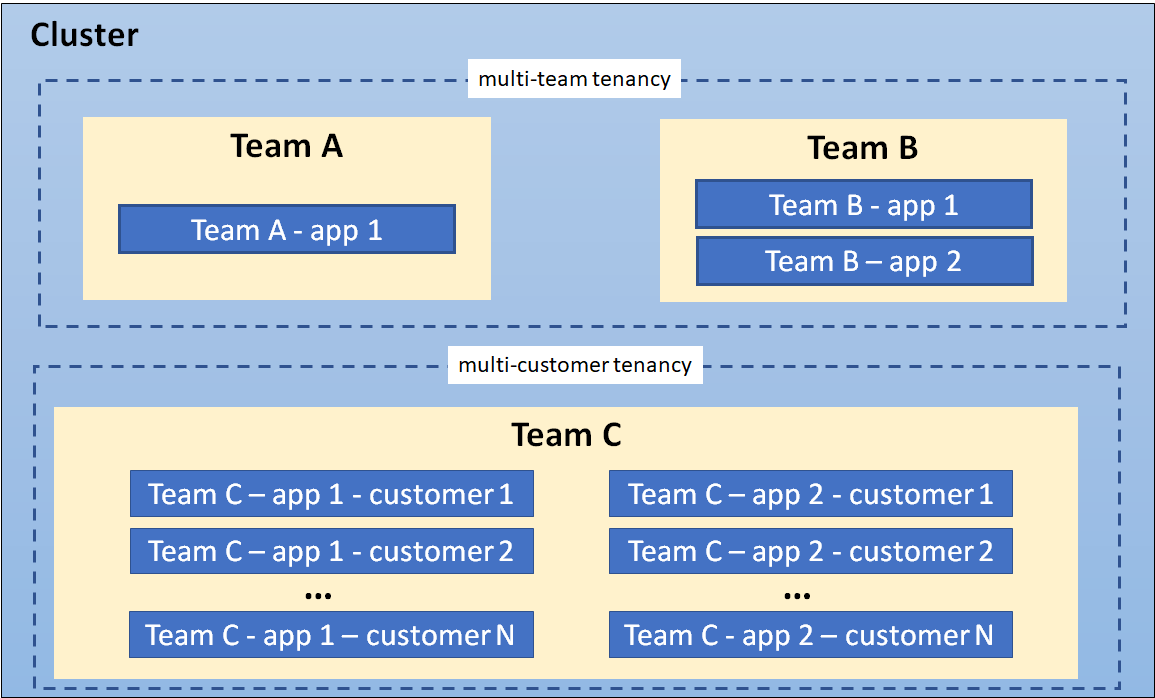
There are a few open-source projects that try to address multi-tenancy issues. These projects are divided into two groups. One of them proposes dividing tenants by namespaces, while the other one proposes providing a virtual control plane to each tenant.
Namespace Per Tenant
Is an approach in Kubernetes multi-tenancy where each tenant or customer is allocated their own dedicated namespace within the Kubernetes cluster. This approach provides a logical and isolated environment for each tenant, allowing them to manage their applications and resources independently.
With the “Namespace Per Tenant” approach, each tenant operates within their own namespace, which acts as a virtual cluster within the larger Kubernetes cluster. The namespace encapsulates all the resources associated with the tenant, such as pods, services, deployments, and persistent volumes.
However, this approach has its limitations. The management difficulty may be increased as subdividing tenants in a granular level of team and application is very hard to accomplish. To address this, Kubernetes has officially provided a controller that supports hierarchical namespaces. Third-party open-source projects such as Capsule and Kiosk also provide more sophisticated multi-tenant support.
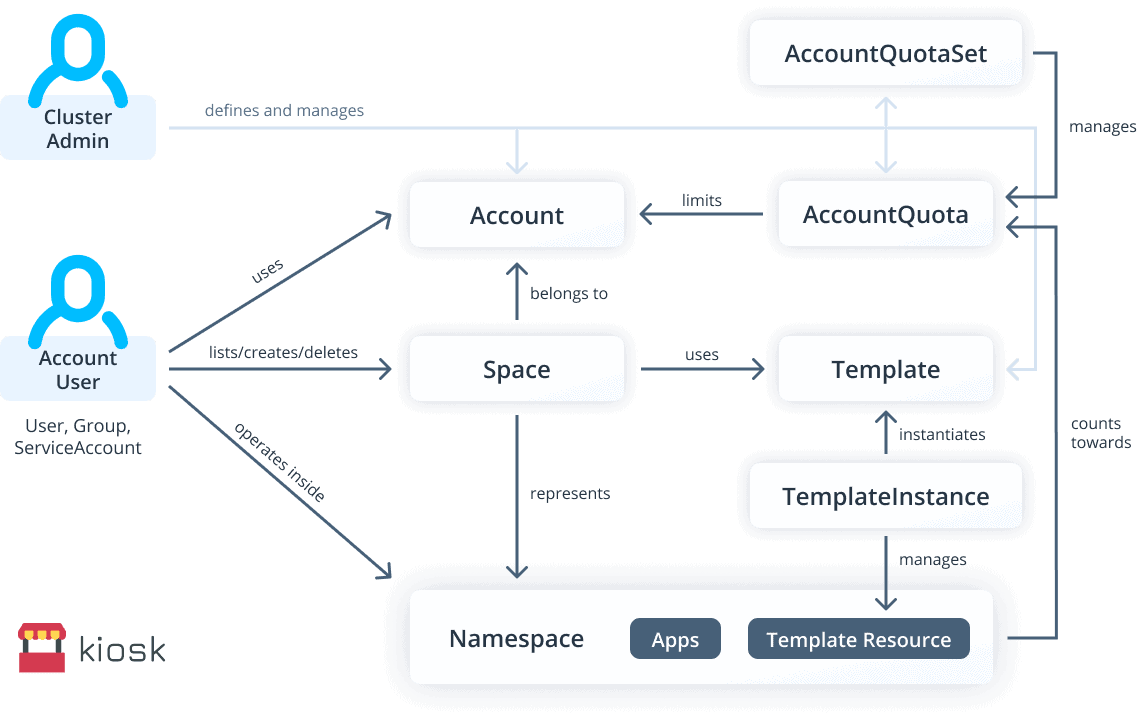
For example, Capsule is designed as a micro-services-based ecosystem that implements a multi-tenant and policy-based environment in your Kubernetes cluster. Multiple namespaces are aggregated in a lightweight abstraction called Tenant (i.e. a grouping of K8s Namespaces). And within each such tenant, users are free to create their namespaces and share all the assigned resources.
And Kiosk uses Kubernetes namespaces as isolated workspaces. This allows tenant applications to run isolated from each other. Cluster admins make initial kiosk setup and after it becomes a self-service system for provisioning Kubernetes namespaces for users.
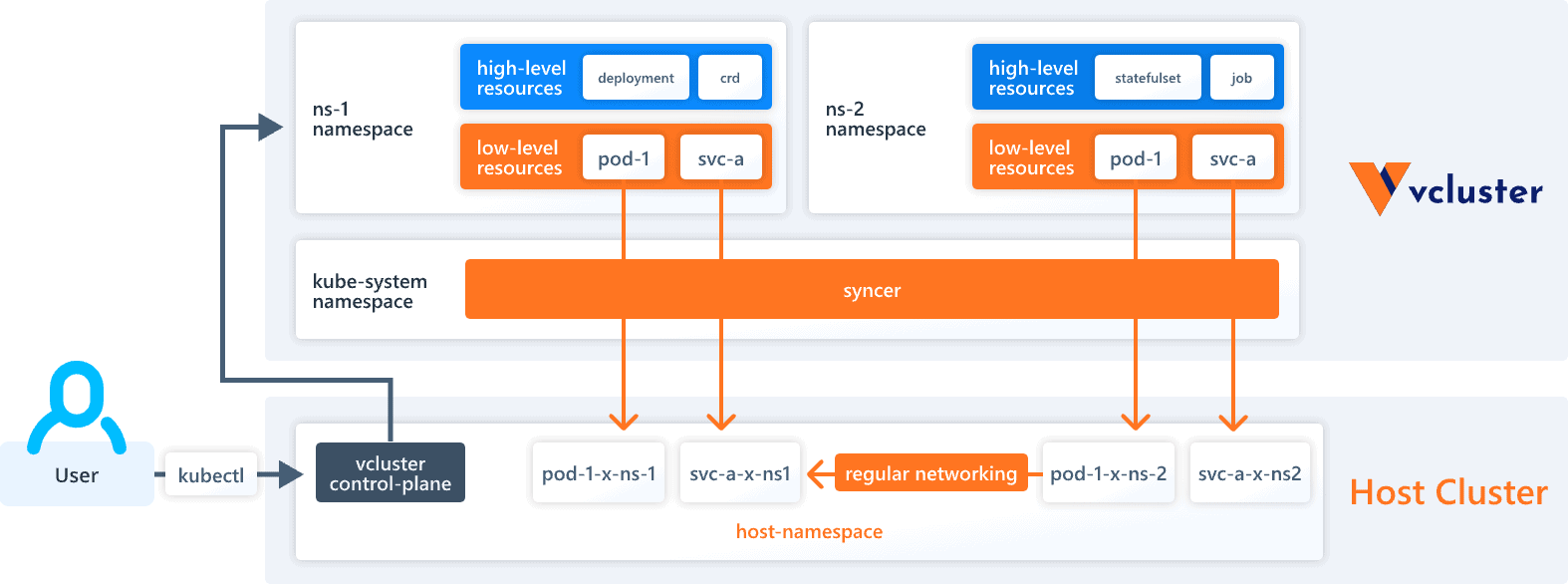
Providing a virtual control plane to tenants
Providing a virtual control plane to tenants in Kubernetes multi-tenancy involves creating isolated instances of control plane components for each tenant or group of tenants. This approach allows tenants to have their own dedicated management layer within the Kubernetes cluster, providing independent control and management capabilities.
This can be implemented by running a separate set of API servers for each tenant, while using the controller to synchronize resources from the tenant apiservers to the original Kubernetes cluster. Each tenant will only have access to its corresponding API server. Apiservers that belong to the original Kubernetes cluster should not be accessible externally.
Virtual control planes usually require a higher resource consumption for the radical isolation of control planes. But, it becomes a more thorough and secure multi-tenant solution when used together with data plane isolation techniques. One example of this is the vcluster project.
Conclusion
Out-of-the-box Kubernetes has no proper multi-tenancy capabilities, but it provides basic support required for accommodating multiple tenants on a single cluster. It is possible to achieve better separation when combining the native K8s features with some third-party tools. All of which obviously comes with additional learning and implementing efforts.
In conclusion, Kubernetes multi-tenancy offers multiple advantages, such as resource consolidation, improved resource utilization, and simplified management of multiple tenants within a single cluster. It enables organizations to achieve efficient resource sharing, cost savings, and streamlined operations. However, the default K8s capabilities are often insufficient for advanced use-cases and additional features come with operational challenges.
Are you looking to provide secure multi-tenancy in your Kubernetes clusters? Not sure which container runtime or CNI to use for sensitive workloads? Reach out to get advice from a team of Kubernetes Certified professionals.

